Reverse DNS
Problem: EMails to services such as AOL or Yahoo get
returned. These services check for the presence of a Reverse DNS setting,
to prevent email from spammers. Otherwise the DNS of the service provider,
such as Covad or Natel is returned, resulting in a mismatch.
----- Original Message -----
From: "Postmaster" <postmaster@CICorp.com>
To: <rick@cicorp.com>
Sent: Friday, April 06, 2007 8:03 AM
Subject: [Norton AntiSpam] Undeliverable Mail
> Unknown host: WSHADDOCK@aol.com
>
> Original message follows.
>
> Received: from fs6 [67.55.221.6] by CICorp.com with ESMTP
> (SMTPD32-7.15) id A6C63E020C; Fri, 06 Apr 2007 08:02:14 -0400
> Message-ID: <016701c7784c$63b76740$06dd3743@fs6>
> From: "Rick Shaddock" <rick@cicorp.com>
> To: <WSHADDOCK@aol.com>
> Subject: DonaldHall.org
> Date: Fri, 6 Apr 2007 08:05:58 -0500
>
> This is a multi-part message in MIME format.
>
> ------=_NextPart_000_015F_01C77822.69100FF0
> Content-Type: text/plain;
> charset="iso-8859-1"
> Content-Transfer-Encoding: quoted-printable
>
> That is a great speech you gave, Dad. It was so much fun to go to Lake
> Loughborough for fishing. |
Detection: DNSReport.com has a free service to detect
problems with a web site's setup.
|
PASS |
Multiple MX records |
OK. You have multiple MX records. This means that if one is down or
unreachable, the other(s) will be able to accept mail for you. |
|
PASS |
Differing MX-A records |
OK. I did not detect differing IPs for your MX records (this would happen if
your DNS servers return different IPs than the DNS servers that are
authoritative for the hostname in your MX records). |
|
PASS |
Duplicate MX records |
OK. You do not have any duplicate MX records (pointing to the same IP).
Although technically valid, duplicate MX records can cause a lot of
confusion, and waste resources. |
|
FAIL |
Reverse DNS entries for MX records |
ERROR: The IP of one or more of your mail server(s) have no reverse DNS (PTR)
entries/* (if you see "Timeout" below, it may mean that your DNS servers did
not respond fast enough)*/.
RFC1912 2.1 says you
should have a reverse DNS for all your mail servers. It is strongly urged
that you have them, as many mailservers will not accept mail from
mailservers with no reverse DNS entry.
You can double-check using the 'Reverse DNS Lookup' tool at the
DNSstuff site if you recently changed
your reverse DNS entry (it contacts your servers in real time; the reverse
DNS lookups in the DNS report use our local caching DNS server). The problem
MX records are:
210.221.55.67.in-addr.arpa [No reverse DNS entry (rcode: 3 ancount: 0) (check
it)] |
Solution: Setting up Reverse DNS
Reverse DNS (rDNS) is quite simply the method of resolving an IP address into a
domain name, just as the domain name system (DNS) resolves domain names into
associated IP addresses.
This tutorial will guide you through setting up reverse DNS in DNS Made Easy.
Step1
First you will need to find out who owns your IP block (usually this is your ISP
or hosting provider). You will need this as they will have to delegate your IP
block to the DNS Made Easy name servers for reverse DNS resolution. If they will
not delegate the IPs to DNS Made Easy then there is no reason to continue and
you can ask them to set the reverse DNS for you.
Just as your Domain is delegated to use DNS Made Easy nameservers (by notifying
your registrar) so must your IP block. Usually an ISP or hosting company will
only do this if you have 256 IPs (a full class C) or more, but some companies
have been known to make an exception.
Once your ISP or hosting company has agreed that they will assign the reverse
DNS to DNS Made Easy ask them for the zone name that you will need to create.
A reverse DNS zone is slightly different than a normal domain name.
The zone (domain) "1.168.192.in-addr.arpa" would actually be the reverse DNS for
the 192.168.1 class C. So this would handle the reverse DNS for IPs 192.168.1.1
to 192.168.1.256.
If your IP block is smaller than a class C then your zone (domain) might look
like this "0/25.1.168.192.in-addr.arpa" or "0-25.1.168.192.in-addr.arpa". These
would actually be the zone that would handle 128 IPs. This would actually be the
zone for the IPs 192.168.1.1 to 192.168.1.128.
Step 2
Add your zone (domain) into the DNS Made Easy system. This is done just as you
would by entering any domain into the DNS Made Easy system. NOTE: You will not
want to use any Domain wizards as they will not really help you. You can just
use the classic Domain setup.
At the end of adding your domain to the DNS Made Easy system you will be
assigned a group of name servers. These are the name servers that you will want
to tell your ISP or hosting company to delegate the reverse DNS to.
Step 3
Tell your ISP or your hosting provider the name servers that they will have to
delegate your IPs to. This is important that they do this. This step is exactly
the same idea when you tell your regsitrar to use DNS Made Easy nameservers for
your doamin.
Step 4
You will then want to add PTR records as needed.
So if you had the zone (domain) "1.168.192.in-addr.arpa" and you created a PTR
record with the following values:
Name: '32'
Value: 'systems.example.com.'
Then the end result would be that the reverse DNS for the IP 192.168.1.32 will
be "systems.example.com.".
That's about it. Adding reverse DNS to your IPs is really easy with DNS Made
Easy!
Location: United States [City: Fairfield, Iowa]
Preparation:
The reverse DNS entry for an IP is found by reversing the IP, adding it to "in-addr.arpa",
and looking up the PTR record.
So, the reverse DNS entry for 67.55.221.210 is found by looking up the PTR
record for
210.221.55.67.in-addr.arpa.
All DNS requests start by asking the root servers, and they let us know what to
do next.
See How Reverse DNS Lookups Work for more information.
How I am searching:
Asking h.root-servers.net for 210.221.55.67.in-addr.arpa PTR record:
h.root-servers.net says to go to figwort.arin.net. (zone: 67.in-addr.arpa.)
Asking figwort.arin.net. for 210.221.55.67.in-addr.arpa PTR record:
figwort.arin.net [192.42.93.32] says to go to NS1.NATEL.NET. (zone:
221.55.67.in-addr.arpa.)
Asking NS1.NATEL.NET. for 210.221.55.67.in-addr.arpa PTR record: Reports that no
PTR records exist [from 207.177.74.108].
Answer:
No PTR records exist for 67.55.221.210. [Neg TTL=86400 seconds]
Details:
NS1.NATEL.NET. (an authoritative nameserver for 221.55.67.in-addr.arpa., which
is in charge of the reverse DNS for 67.55.221.210)
says that there are no PTR records for 67.55.221.210.
To get reverse DNS set up for 67.55.221.210, you need to speak to your Internet
provider. You could also
check with dns@natel.net., who is in charge of the 221.55.67.in-addr.arpa. zone.
Note that all Internet accessible hosts are expected to have a reverse DNS entry
(per RFC1912 2.1),
and many mailservers (such as AOL) will likely block E-mail from mailservers
with no reverse DNS entry.
To see the reverse DNS traversal, to make sure that all DNS servers are
reporting the correct results, you can Click Here. |
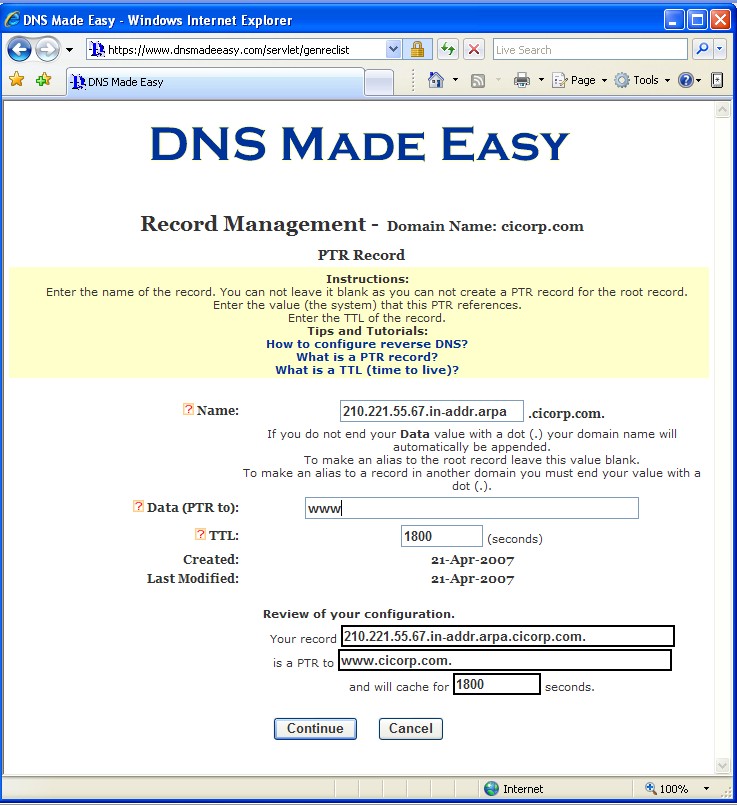
How This Applies to C I Corporation
| Domain |
IP |
Reverse DNS |
| mail.CICorp.com |
67.55.221.210 |
210.221.55.67 |
| PTR Record Name: |
10 |
|
| Date (PTR to): |
www.cicorp.com |
|
| TTL |
1800 seconds |
|
We can check this with
DNSReport.com
DNS Made Easy
PTR Record (Pointer Record)
Pointer records are used to map a network interface (IP) to a host name. These
are primarily used for reverse DNS.
Example Input for Domain Name: 1.168.192.in-addr.arpa
Name: 25
Data (PTR to): www.example.com.
TTL: 1800 seconds
Result:
This will create a reverse DNS entry for 192.168.1.25. The reverse DNS will be a
pointer to 'www.example.com.'. This record will have a cache (TTL) of 30
minutes.
Of course 192.168.1.x is an internal network and would not be allowed in the DNS
Made Easy system.
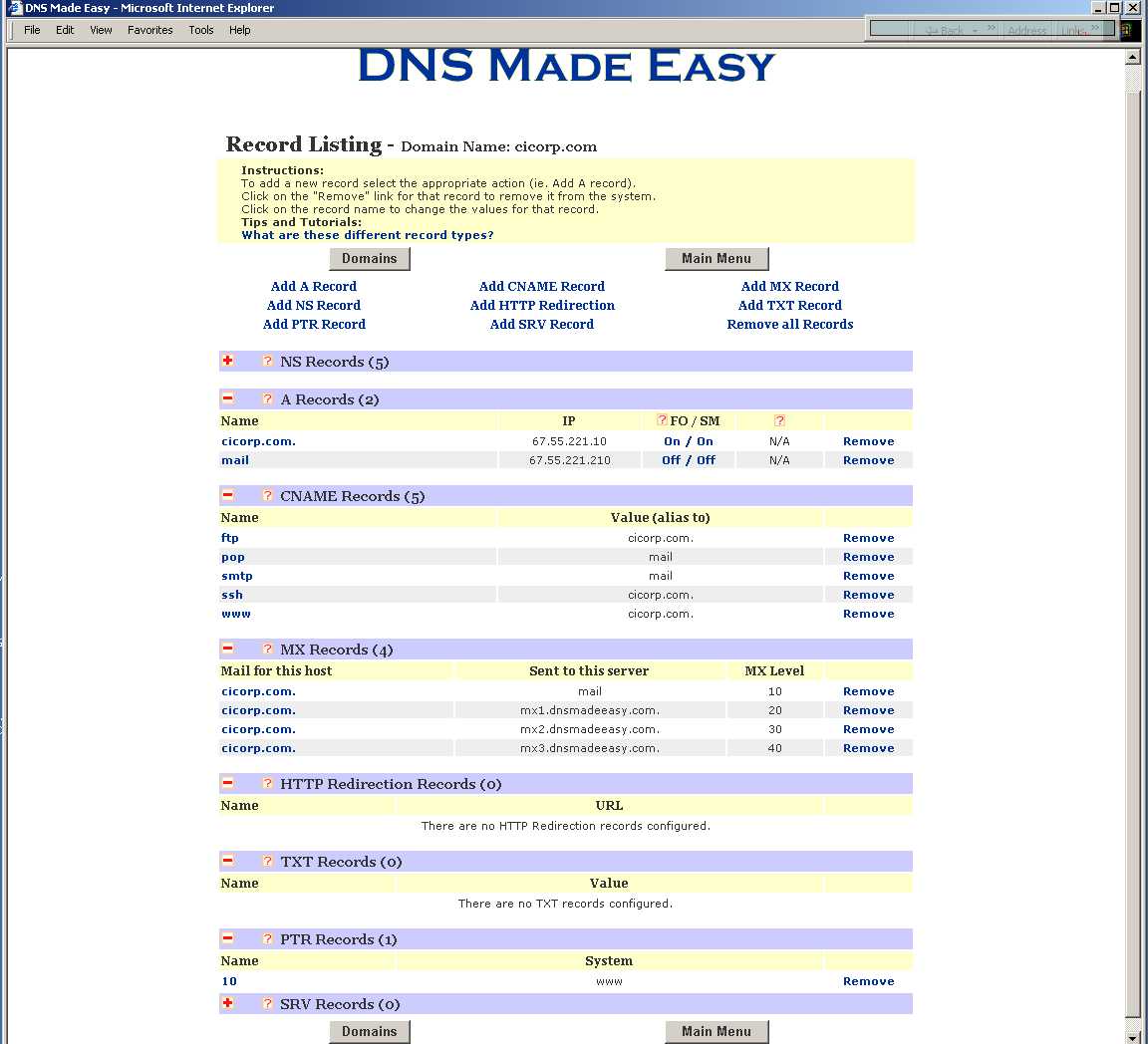
Here is the screen that DNS Made Easy provides for changing the
PTR record to implement Reverse DNS. This did not work, so we need
to find out how to properly fill out the following screen.